Configure Versasec CMS with Securosys HSM
The vSEC:CMS makes use of the PKCS#11 interface available in the HSM to utilize the benefits of the HSM key storage and generation. Follow the below shown steps to configure Versasec vSEC:CMS to work with Primus HSM or CloudHSM.
It is expected at this point that the Primus HSM PKCS#11 provider is installed and configured to connect to the HSM on the server where the vSEC:CMS is installed. See Primus HSM PKCS#11 Provider for more information. vSEC:CMS will search in the system path for the PKCS#11 module.
Visit vSEC:CMS HSM Support on the Versasec online documentation for more details.
-
From
Options - Connectionsclick theConfigurebutton. Make sure that theHardware Security Module (HSM)is in the selected window. -
Click
Hardware Security Module (HSM)and click theAddbutton to setup a template.- Enter a template name and from the drop-down list select the Securosys Primus HSM.Moin
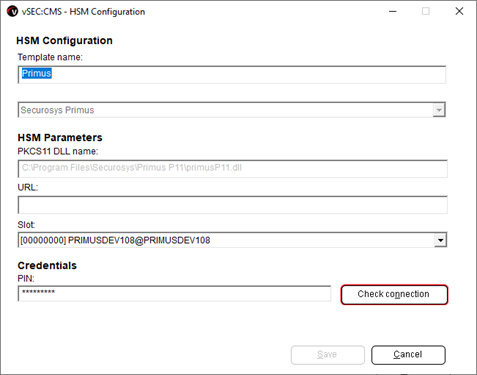
-
The PKSC#11 module will be automatically detected and populated into the
PKCS11 DLL namefield. The URL will be read from the configuration file that is included as part of the Primus HSM PKCS#11 provider configuration file.- Select the
SLOT, where the master key will reside in, from the available slot list in the drop-down list. See Primus HSM PKCS#11 Provider - Configuration - Section Slots on more information about PKCS#11 slots. - Enter the PKCS#11 PIN credential for the user who has access to the slot and click
Check connectionto test connectivity. If connectivity to the HSM is successful a success dialog will pop-up.
infoObtain the PKCS#11 Password (PIN) from your HSM administrator. In case of CloudHSM subscription the PKCS#11 credentials are provided during the on-boarding procedure. See Primus HSM PKCS#11 Provider - Primus HSM Configuration - Preparing the PKCS#11 Password (PIN).
- Select the
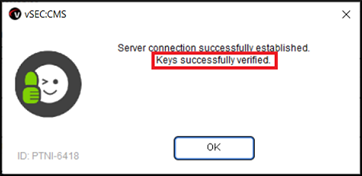
Example successful connection pop-up:
Click Save to save and close the configuration.
- Once the connection is setup it will be necessary to create an
Operator Service Key Store(OSKS). Navigate toOptions - Operatorsand click theAdd service key storebutton. Enter a name in theStore namefield and clickAdd.
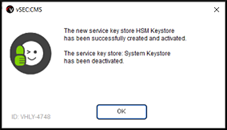
All vSEC:CMS master keys will be copied to the HSM during this process and at the end you will get a success dialog.

From the Operators table you can see that the HSM is now used as key store as indicated by the * character.
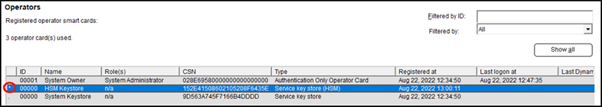
Additionally, if you go back to Options - Connections - Hardware Security Module (HSM) and select your HSM connector and Edit, then click the Check connection button you should see more information in the success dialog indicating that the master key used by vSEC:CMS was found in the slot on the HSM.
- It is strongly recommended to generate a new master key. From
Options - Master Keyclick theGenerate new master keybutton to start the process.
It is important to remember that any new credential administration key will be diversified from the newly generated master key. Any credential administration key diversified from older master key(s) of the vSEC:CMS application will remain operable. However, it is recommended to re-register those credentials issued from the older master key(s) of the vSEC:CMS. This will update the user's credential administration key so that it is diversified from the new master key.
- Select the option
On server side HSMand from the drop-down list 3 options are available,DES-EDE3,AES128andAES256. Select the appropriate key type and size as required for your environment.
It is recommended to select AES for key type as DES has been withdrawn as a standard by the National Institute of Standards and Technology. From version 6.5 of vSEC:CMS it is possible to migrate from DES managed master keys to AES.
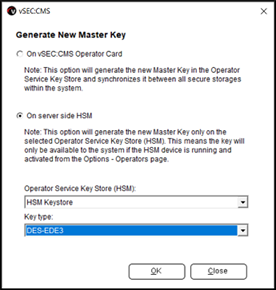
Click Ok. A dialog will popup informing you about the change to the system. Click Yes to complete the setup.
- Navigate to
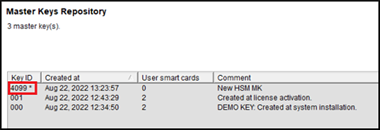
Repository - Master keysand you will see the entry. The*character indicates which master key is to be used by vSEC:CMS.
Additionally, from Repository - Smart Cards you will see that credentials managed by older master keys will have an Update needed message.
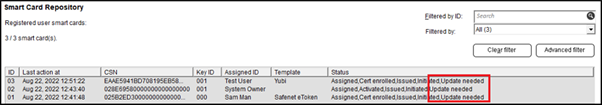
Once the HSM master key is generated it will not be possible to roll back to use an earlier master key. For any credential that was previously managed by the vSEC:CMS with an older master key that was not generated by the HSM it will be possible to continue to manage these credentials, but it is recommended to update these credentials so that they will be managed by the newly created master key.
Credentials whose master key needs to be updated can be done as described below:
- From vSEC:CMS
Admin consolenavigate toActions - Smart Card Updateand attach a credential that needs to be updated and click theExecutebutton; - From a client host that has vSEC:CMS User installed and configured for updates, navigate to the
Updatetab to perform the update.
Additional Information
Any master key added to the HSM will have a label starting with CMS MK on the HSM. Depending on whether the master key is generated only on the HSM or was a key created and stored on a full-featured operator card and synced with the HSM, the label will have a different value depending on which option is selected.
For a master key generated only on the HSM the label on the HSM will be: CMS MK 4099 (this is a hex value), if this was the first key. Any additional key(s) would be incremented by one; therefore, a second master key would have a value of CMS MK 4100 and so on.
For a master key created and stored on a full-featured operator card and synced with the HSM the label on the HSM will be: CMS MK 00, if this was the first key. Any additional key(s) would be incremented by one; therefore, a second master key would have a value of CMS MK 01 and so on.